OVERVIEW
The site im.vc currently has a traffic classification of zero (the lower the superior). We have downloaded twenty pages within the website im.vc and found one website referring to im.vc.
Pages Parsed
20Links to this site
1IM.VC TRAFFIC
The site im.vc has seen fluctuating levels of traffic throughout the the year.
Date Range
1 week
1 month
3 months
This Year
Last Year
All time
Date Range
All time
This Year
Last Year
Date Range
All time
This Year
Last Year
Last Month
LINKS TO IM.VC
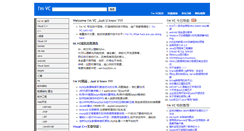
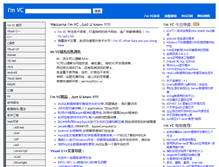
WHAT DOES IM.VC LOOK LIKE?
IM.VC SERVER
We identified that the main root page on im.vc took one thousand and forty-eight milliseconds to come up. We could not find a SSL certificate, so in conclusion our web crawlers consider im.vc not secure.
Load time
1.048 sec
SSL
NOT SECURE
IP
162.159.208.98
FAVICON

SERVER SOFTWARE
We detected that this domain is weilding the yunjiasu-nginx os.SITE TITLE
Im VC - Just U know YDESCRIPTION
Im VC以PARSED CONTENT
The site im.vc states the following, "Welcome Im VC ,Just U know Y! Im VC 专注技术领域打造纯粹的技术网站连广告都懒得挂 Im VC,Lets GO." I noticed that the webpage stated " 海量技术文章助您快速提升技术水平 Im VC,What are you doing here." They also stated " Im VC精品Just U know Y! Sybase ASE for Linux安装过程及安全配置. COM 组件设计与应用五 用 ATL 写第一个组件. C Design Patterns 2 - Strategy. Enterprise Library Step By Step系列 十五 配置应用程. UMLRUP 和 Zachman 框架 完美结合. 自然框架 之表单控件 一 实体类 Class. 第四节- 构造函数和析构函数 - Classes and Objects." The meta header had IM as the first keyword. This keyword was followed by VC, 技术, and 文章 which isn't as important as IM. The other words the site used was Java. PHP is also included but could not be understood by search engines.SEE MORE WEB SITES
webnocular.com
To purchase, call Afternic. com at 1 781-373-6847 or 855-201-2286. Click here for more details.
Anthem Remote Access VPN
This is a restricted computer system and is for authorized use only. Failure to maintain the confidentiality of sensitive information may subject the user to penalties under applicable laws. By using this system, the user consents to monitoring, inspection and disclosure of all activity for security purposes.